It is hardly news: the digitisation of day-to-day business life is increasing, as the DsiN security monitor 2016 shows in its statistics*. At the same time, some 60% of respondents say that they are not aware of the risks and legal requirements regarding use of the Internet and e-mails. This uncertainty is also reflected in the use of appropriate protective measures, which - unlike the increasing digitisation - are remaining unchanged. For example, still less than half (48 percent) of respondents are taking measures to ensure email security.
Where does the encryption fatigue come from?
Hans-Joachim Giegerich, Managing Director of Giegerich & Partner, knows the concerns and needs of companies from his discussions with clients of the internal email encryption add-in gpg4o (www.gpg4o.de): "The hesitancy is usually due to the fact that the responsible person thinks the topic too complex or the users simply do not cooperate. Many employees are aware of the importance and welcome encryption, but one must also remember that security is not free. Employees have to leave their comfort zone and for this it is necessary to motivate and guide them. Our task as a provider is to further improve usability in order to make it easier for employees to adapt their processes and behaviour. With the current version of gpg4o, we have effectively reached this goal. Version 5.1. contains only minor optimisations and bug fixes. We have implemented the most important usability requirements of our customers in recent years."
Poetry and Truth: Arguments against email encryption challenged
Apart from the supposedly high expense and the question of user friendliness, other aspects also play a role in the hesitancy about encryption. There is often a diffuse collection of fears and ignorance about the state of the art in this area. Prof. Dr. Friedemann Vogel, junior professor of media linguistics at the University of Freiburg, has already devoted extensive attention to the "prejudices and myths about message encryption". In what follows, Giegerich & Partner has compiled an overview of the most frequently used arguments against encryption and given them a reality check.
The six key arguments against email encryption under the microscope
1. Organisation: "Email encryption is complex!"
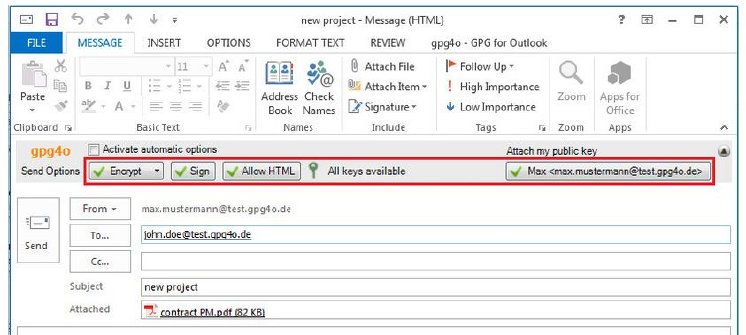
Of course, encryption is not possible without preparation. Companies above all need to think about the secure management and organisation of email encryption. This includes topics such as the secure archiving of e-mails, roles and rights, and, above all, the administration of the keys, which could otherwise be a weak point. The expenditure for this varies with the programmes used. If they are aligned for companies, they typically have user-friendly administrator features, such as a central key server. In addition, IT administrators usually implement "email" encryption programmes without prior knowledge. The user himself decides, when sending, with a simple click, whether the email is to be encrypted or unencrypted (Figure 1).
2. Costs: "Email encryption is expensive!"
For private users, there are numerous freeware solutions that have the necessary functionality. For example, Giegerich & Partner offers its Outlook encryption add-in gpg4o for private users free of charge (www.giepa.de/...). The implementation requires only a few clicks in the case of gpg4o and can also be connected to a large number of users with little effort for IT administrators. For companies, operating costs depend on the number of users. For a medium-scaled company with around 25 employees, the licensing costs of gpg4o per employee are around 65 € per year. These costs are counterbalanced by the potential (image) damage caused by business secrets, customer data or patent information that fall into the wrong hands.
3. Security: "Any email encryption can be cracked!"
Theoretically this is true, but in practice even the secret services do not have unlimited time and financial resources at their disposal. In this spirit, bicycle locks are also considered to be theft-proof on the basis of a "cracking" time of three minutes. With modern encryption standards, such as AES-256, it takes billions of years to decrypt the codes, even with the fastest computers available. That is why it is so important to manage the keys, together with high-quality passphrases and access to systems, since they are the point of attack for hackers. If users and administrators adhere to the security standards, they have nothing to worry about. One thing, however, should always be kept in mind: the sender, the addressee and the subject are generally not encrypted at PGP and should therefore be considered visible to everyone in the event of doubt. The subject should therefore not contain any protected information.
4. Need: "We have nothing important to hide!"
In the past, this argument has mainly been used to justify legislative initiatives on surveillance. But, especially in the case of companies, customer and employee data are already part of sensitive and thus classified data, not to mention information on prototypes or technological secrets. Simply sustaining a data leak in public can seriously damage the company's reputation. Even private individuals often do not realise what it means, for example, if their correspondence with their lawyer or tax consultant falls into the wrong hands. The argument "anyone who encrypts makes himself suspicious" makes no sense. Encryption in companies is primarily used to protect against cyber criminality and is therefore just as legitimate as it is necessary. Accordingly, the state also supports appropriate security activities, for example with the initiative by the Federal Government to make Germany "encryption site No. 1 worldwide".
5. Spreading: "Email encryption is not widespread!"
Probably the most classic argument against email encryption is the chicken-and-egg problem: "If you do not encrypt, I will also not encrypt". The day-to-day experience at Giegerich & Partner shows this clearly: customers, service providers and cooperation partners are generally opposed to the proposal to encrypt standard correspondence. You just have to propose it to all communication at the same time. In addition, most encryption solutions are compatible with industry standards. For example, gpg4o has been able to properly verify PGP/MIME-signed email since version 3.4, ensuring compatibility with applications such as GPGMail and many others. This simplifies the encrypted communication and therefore ensures a higher acceptance of encryption software in general.
6. Law: "Email encryption is not always allowed!"
Although strong cryptography is still subject to criticism in the US and many other countries, the encryption of data is generally permitted in Europe. In some cases, it is even possible to see an obligation, or at least a recommendation, of encryption in the laws and regulations on data protection - which companies are subject to. A very recent example is the European Data Protection Regulation (EU-DSGVO). So he who encrypts is simply more secure.
Most arguments against the use of email encryption can therefore be refuted. But this presupposes that companies and employees actively participate in the implementation and the fundamental safety standards are complied with. Because in the end as always: without the user there is nothing.
*Source: DsiN Security Monitor 2016 Mittelstand, p. 8, www.sicher-im-netz.de/...
**Source: virtual-privacy.org/index.php/verschluesselung-vorurteile-und-maerchen